OpenVPN
OpenVPN setup notes - ported from old wiki (unedited).
Client
Configuration file template
connection.ovpn:
client
dev tap
proto udp
remote remote.host.domain 1194
resolv-retry infinite
nobind
persist-key
persist-tun
comp-lzo
verb 3
<ca>
-----BEGIN CERTIFICATE-----
ca-cert-goes-here
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
client-cert-goes-here
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN RSA PRIVATE KEY-----
client-key-goes-here
-----END RSA PRIVATE KEY-----
</key>
Platforms
OSX
https://tunnelblick.net/downloads.html
Just download and install. Double click on a configuration file to install the profile for use.
Linux - NetworkManager
- Select
Configure VPN... - Click
Add:
- Click
Forward:
- Select
OpenVPN Clientand clickForward:
- Enter the connection details, then click
Advanced:
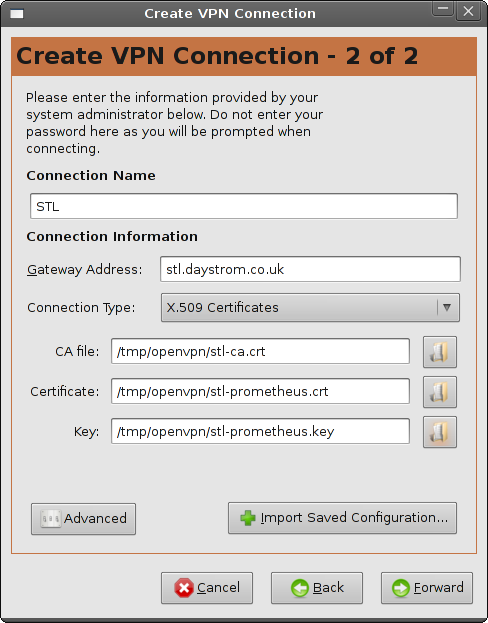
- Enter the advanced options, then click
Ok:
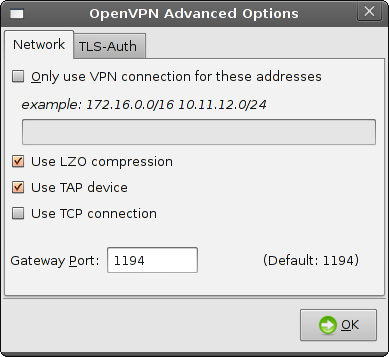
- Click
Forward
Windows
Installing
- Download OpenVPN from http://openvpn.net/index.php/open-source/downloads.html#latest-stable
- Install, accepting the defaults.
- Right click
start→All Programs→OpenVPN→OpenVPN GUIand selectProperties. - On
Compatibilitytab tickRun this program as an administrator. - Click
OK
Configuring
- Click
start→All Programs→OpenVPN→Shortcuts→OpenVPN configuration file directory - Put configuration files in directory to make them available
- On first run:
- Click on the up-arrow on the system tray and select
Customize. - In the drop down next to
OpenVPN GUI for WindowsselectShow icon and notifications. - Click
OK
- Click on the up-arrow on the system tray and select
Usage
- Click
start→All Programs→OpenVPN→OpenVPN GUI. - Right click on the OpenVPN tray icon and select
Connect.
Server
Install - Debian
Install the server:
apt-get install openvpn
Configure
Create the certificates
There are two ways to create the certificates, the EasyRSA method, or if more control is needed manually with OpenSSL. Personally I prefer to know what’s going on so I use OpenSSL.
OpenSSL
See OpenSSL for directions on creating OpenVPN certificates.
EasyRSA
mkdir /tmp/openvpn-cert
cd /tmp/openvpn-cert
cp /usr/share/doc/openvpn/examples/easy-rsa/2.0/* .
vim vars # Configure
source ./vars
./clean-all
./build-ca # Create CA
./build-key-server ds9 # Create server certificate
./build-key prometheus # Create client certificate for my laptop
./build-dh # Generate Diffie Hellman parameters
Copy the certificates to somewhere useful:
mkdir /etc/openvpn/keys
cp keys/ca.* keys/dh1024.pem keys/ds9.crt keys/ds9.key /etc/openvpn/keys/
scp keys/prometheus.crt keys/prometheus.key keys/ca.crt laurence@prometheus: # Securely copy my laptops key to it
# remove the key generating foo
cd
rm -rf /tmp/openvpn-cert
Main configuration
Put this config file into /etc/openvpn/server.conf:
proto udp
dev tun
ca keys/ca.crt
cert keys/ds9.crt
key keys/ds9.key # This file should be kept secret
dh keys/dh1024.pem
server 10.10.10.0 255.255.255.0 # vpn subnet
ifconfig-pool-persist ipp.txt
push "route 192.168.0.0 255.255.255.0" # "Live" subnet
keepalive 10 30
comp-lzo
user nobody
group nogroup
persist-key
persist-tun
verb 10
mute 20